- Top Results
- Bosch Building Technologies
- Security and Safety Knowledge
- Security: Video
- How can be configured BVMS to function in a GDPR compliant organization?
How can be configured BVMS to function in a GDPR compliant organization?
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Question
How can be configured BVMS to function in a GDPR compliant organization?
Answer
The GDPR (General Data Privacy Regulation) is enforced on the 25th of May 2018. As a regulation it is directly applicable to all EU member states without the need for national implementing legislation. As information captured, processed and stored by video surveillance systems is classified as "sensitive" the GDPR will cause significant impact on the video surveillance installations throughout Europe. This article gives insights into the new legislation and describes how a video surveillance system can be designed and configured in order to help an organization comply with this new regulation.
This article describes how the GDPR impacts video surveillance systems and how BVMS can be configured to function in a GDPR compliant organization.
Since the publication of this guide the European Data Protection Board (EDPB) has issued a paper specifically targeted at video surveillance installations: GDPR video surveillance guide.
- Section 1 of the article: will describe the functional requirements as they were extracted from the GDPR by the Bosch legal teams.
- Section 2 of the article: will describe how these functional requirements affect the system design phase of a project.
- Section 3 of the article: will describe how these functional requirements affect the system installation phase of a project.
- Section 4 of the article: lists some general exceptions which are applicable for all video surveillance systems.
Last, but not least, a list with frequently asked questions and a dictionary is included.
General Data Protection Regulation (GDPR)
The full text of the "Position of the Council at first reading with a view to the adoption of a REGULATION OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation)" can be found on the website of the European Union.
Key changes
A description of the key changes can be found on http://www.eugdpr.org/key-changes.html
Information
| Website | Description |
| https://ec.europa.eu/info/ | Official EU website. Stronger rules on data protection mean people have more control over their personal data and businesses benefit from a level playing field. |
| https://edpb.europa.eu/edpb_en | The European Data Protection Board (EDPB) is an independent European body, which contributes to the consistent application of data protection rules throughout the European Union, and promotes cooperation between the EU’s data protection authorities. |
| https://en.wikipedia.org/wiki/General_Data_Protection_Regulation | General Data Protection Regulation on Wikipedia. |
Requirements
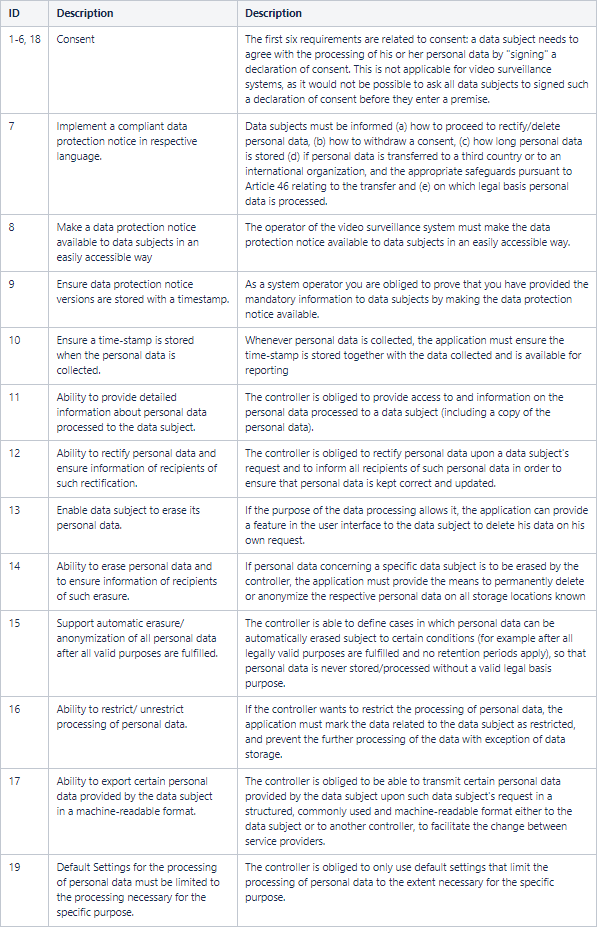
1. Functional requirements
Bosch has analyzed the GDPR. The analysis resulted in the functional requirements listed in the table below. These functional requirements are applicable to all systems that process personal information and not specific for a video management system. The "Description" column describes how the requirement is related to a video surveillance system.
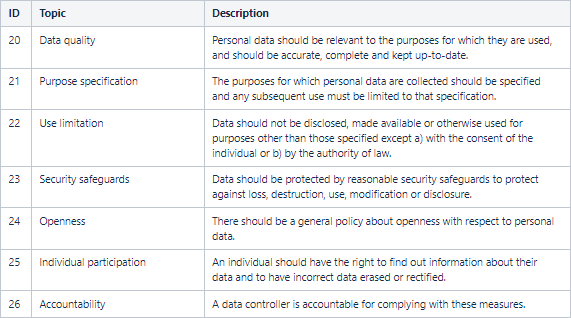
2. Concepts
System design
1. Data protection impact assessment
Next to the requirements of the system itself, article 35 requires an organization to conduct a data protection impact assessment. "Where a type of processing in particular using new technologies, and taking into account the nature, scope, context and purposes of the processing, is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data." Source: GDPR full text, Article 35, section 1 (page 164)
2. Camera positioning
Related to requirement(s): [20,21]
Video cameras should only be installed in areas where they serve a specific goal. The installed location of a camera, which is gathered personal data (or biometric data), should be justified.
3. System resilience
Related to requirement(s): [23]
Hardware mechanisms (RAID, redundant components) as well as software mechanisms (for example dual recording) are available to minimize the chance data is lost.
Hardware mechanisms (access control to rooms, physical locks, and others) as well as software mechanisms (encryption of data, the architecture of the software itself) are available to minimize the chance data is stolen.
System configuration and operation
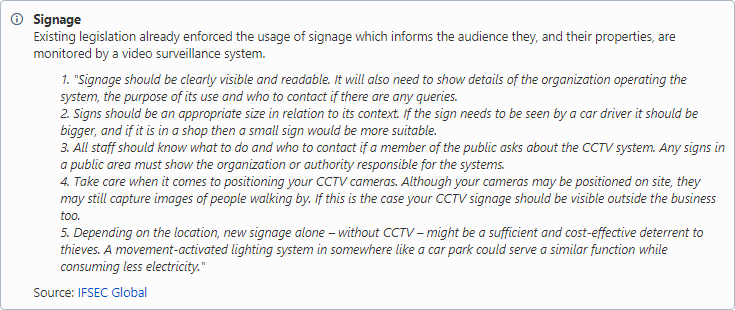
1. Signage
Related to requirement(s): [7,8]
The data protection notice cannot be made easily available to data subjects in the context of a video surveillance system. (IFSEC Global)
2. Time-service
Related to requirement(s): [10]
Offering a reliable time-service to entire video surveillance environment ensures that all the components, such as cameras and software clients, are using the same, synchronized, clock. Bosch provides a recommendation on how to setup a reliable time-service within the video surveillance environment. This recommendation is available on the Bosch Building Technologies community: BVMS - Configure Time services.
3. Video Authentication
Related to requirement(s): [12,20,23]
The video authentication functionality should be enabled. This allows system operators to check (either during export or on the actual recorded video) if (unauthorized) modifications are made to the recorded video footage.
4. Removing personal data
Related to requirement(s): [13,14,15,25]
A self management erasure functionality may be considered only if personal data can be erased without further assessment (for example, regarding retention obligations under applicable tax or commercial law). Summarized: it would not be allowed for people which appear on recorded footage to delete this footage themselves. The system includes a retention time mechanism which automatically removes recorded footage and logbook data after the maximum retention time has passed.
5. Removing biometric data
Related to requirement(s): [13,14,15,25]
A self management erasure functionality may be considered only if personal data can be erased without further assessment (for example, regarding retention obligations under applicable tax or commercial law). Summarized: it would not be allowed for people to delete their own biometric data from the system. The system includes a retention time mechanism which automatically removes biometric data from the logbook as well as a mechanism to remove biometric data manually by anonymizing information in the logbook and removing subjects from the person identification subject list.
6. Restrict access to data
Related to requirement(s): [16]
Access to person and biometric data (recorded video and logbook) can be restricted to specific (groups of) operators.
7. Video Export
Related to requirement(s): [17]
Video footage can be exported in several file formats, proprietary (Bosch) as well as open standards (mov, asf). The proprietary export format can be read by Bosch software, the open standard exports can be read by industry standard software (Apple Quicktime, VLC, Windows Media Player, etc...)
8. Export biometric data
Related to requirement(s): [17]
Biometric data can be exported using the logbook export functionality for operators(groups) who are authorized to do this.
9. User authorizations
Related to requirement(s): [19,22,23]
The system allows complex user rights configurations. This allows a system administrator to give access to specific system components (cameras, sensors, maps) and system functionality (live, recording, alarms, export) to specific operator (groups). Additionally most operator tasks are logged in the system logbook for further reviews
10. System protection
Related to requirement(s): [23]
Bosch recommends implementing the tips mentioned in the data security guidebook to decrease the risk of personal or biometric data being accessed, modified, or destroyed by unauthorized persons.
Exceptions
1. Provide personal information
Related to requirement(s): [11]
At this moment the video surveillance system is not able to identify a person without adding a, separate, person identification system generating biometric data. Personal data can be (theoretically) provided, but would require the operator to manually browse thousands of hours of recorded video. (GDPR full text)
Conclusion
After some intensive discussions with experts on all of these topics, Bosch has concluded that the current video surveillance products (including cameras, software and recording hardware) will allow an organization to be GDPR "compliant".
Frequently asked questions
The questions and answers below are gathered from several sources for the readers convenience. At the moment of writing this article the answers are valid.
|
Question
|
Answer
|
Source
|
|---|---|---|
| Who does the GDPR affect? | "The GDPR not only applies to organizations located within the EU but it will also apply to organizations located outside of the EU if they offer goods or services to, or monitor the behavior of, EU data subjects. It applies to all companies processing and holding the personal data of data subjects residing in the European Union, regardless of the company’s location." |
https://www.eugdpr.org/gdpr-faqs.html |
| Does my business need to appoint a Data Protection Officer (DPO)? |
"DPOs must be appointed in the case of: (a) public authorities, (b) organizations that engage in large scale systematic monitoring, or (c) organizations that engage in large scale processing of sensitive personal data (Art. 37). If your organization doesn’t fall into one of these categories, then you do not need to appoint a DPO." |
https://www.eugdpr.org/gdpr-faqs.html |
| What is considered as "sensitive personal data"? | "Personal data which are, by their nature, particularly sensitive in relation to fundamental rights and freedoms merit specific protection as the context of their processing could create significant risks to the fundamental rights and freedoms. Those personal data should include personal data revealing racial or ethnic origin,..." |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
| What is considered as "biometric data"? | "Biometric data' means personal data resulting from specific technical processing relating to the physical, physiological or behavioral characteristics of a natural person, which allow or confirm the unique identification of that natural person, such as facial images or dactyloscopic data;" |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
| Are images captured by a video surveillance system considered as sensitive personal data? |
Yes, as a photo can reveal racial or ethnic origin this information is considered sensitive. |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
| Does the GDPR require the system to anonymize all data subjects by using of "pixelization"? |
Pixelization is a technique whereby any moving object appearing in front of a video surveillance camera is blurred. In the context of the GDPR this process is called pseudonymisation. In contrast to what is marketed by many, data subjects do not have to be anonymized and therefore the use of pixelization software is not required. However, "Where the processing for a purpose other than that for which the personal data have been collected is not based on the data subject's consent... the controller shall...take into account: the existence of appropriate safeguards, which may include encryption or pseudonymisation." Summarized and put into context: if the position of a camera cannot be justified, pseudonymisation may be used to keep a legal basis for the position of that specific camera. |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
| How does GDPR influence the deployment of person identification? |
According to article 9 the processing of biometric data is prohibited: "Processing of personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade-union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person's sex life or sexual orientation shall be prohibited." |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
| Does GDPR allow processing of biometric data at all? |
GDPR only allows processing biometric data based on the description of article 9 section 2, in which exceptions on article 9 section 1 are described. |
https://data.consilium.europa.eu/doc/document/ST-5419-2016-INIT/en/pdf |
Dictionary
This section provides some important definitions of terms. The source of these definitions, and all other definitions, can be found in: GDPR full text Article 4, page 112.
|
Term
|
Definition
|
|---|---|
| Controller | "The natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; where the purposes and means of such processing are determined by Union or Member State law, the controller or the specific criteria for its nomination may be provided for by Union or Member State law;" |
| Data subject | "...identified or identifiable natural person..." |
| Personal data | "Any information relating to an identified or identifiable natural person ('data subject'); an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person; |
| Processing | "...means any operation or set of operations which is performed on personal data or on sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction;" |
| Pseudonymisation | "...means the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information, provided that such additional information is kept separately and is subject to technical and organizational measures to ensure that the personal data are not attributed to an identified or identifiable natural person;" |
Still looking for something?
- Top Results