- Top Results
- Bosch Building Technologies
- Security and Safety Knowledge
- Security: Video
- Bosch Security Advisories - PSIRT (Product Security Incident Response Team)
Bosch Security Advisories - PSIRT (Product Security Incident Response Team)
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This article contains the list of Security Advisories (SA) to inform you about identified security vulnerabilities in our product or service and proposed solutions.
🔔 Subscribe to this article and Stay up to date with the latest published Security Advisories.
2024
|
Advisory number |
Title |
Affected Products |
Summary |
|
Publication
|
Unrestricted resource consumption in BVMS
|
|
A vulnerability has been identified in the Bosch VMS Central Server concerning unrestricted resource consumption, leading to excessive use of disk space. The uncontrolled resource consumption can lead to a significant impact on the availability and performance of the affected system. This can result in the inability to store new data, process incoming requests, and perform essential system functions. In severe cases, it may lead to system crashes and data loss.
|
|
Publication |
Sensitive information disclosure in Bosch Configuration Manager |
Bosch Bosch Configuration Manager |
A vulnerability was discovered during internal testing of the Bosch Configuration Manager, which may temporarily store sensitive information of the configured system. |
|
Publication |
Unauthenticated information leak in Bosch IP cameras |
Bosch Camera Firmware |
A vulnerability was discovered in internal testing of Bosch IP cameras of families CPP13 and CPP14, that allows an unauthenticated attacker to retrieve video analytics event data. No video data is leaked through this vulnerability. |
| BOSCH-SA-587194-BT
Publication
|
Multiple Curl vulnerabilities in the Git for Windows component of Bosch DIVAR IP all-in-one Devices
|
|
DIVAR IP System Manager is a central user interface that provides an easy system setup, configuration and application software upgrades through an easily accessible web-based application.
Multiple Curl vulnerabilities in the Git for Windows component have been discovered in DIVAR IP System Manager versions prior to 2.3.2, affecting several Bosch DIVAR IP all-in-one models.
|
|
Publication
|
BVMS affected by Autodesk Design Review Multiple Vulnerabilities
|
|
BVMS was using Autodesk Design Review for showing 2D/3D files. Autodesk has published multiple vulnerabilities which when successfully exploited could lead to the execution of arbitrary code. Starting from BVMS version 11.0, the Autodesk Design Review is not used anymore in BVMS, but the BVMS setup does not uninstall the Autodesk Design Review during a BVMS upgrade. This means only BVMS systems are affected which have versions <= 10.1.1.12 or were upgraded from BVMS Version <= 10.1.1.12 to a higher version.
Before removing Autodesk Design Review v 9.1.0.127 make sure that it is not used by any other software installed on that machine. How to check if the system is affected:
|
| BOSCH-SA-090577-BT Publication
|
Multiple OpenSSL vulnerabilities in BVMS
|
|
BVMS is using a Device Adapter service for communication with Tattile cameras which is also active when no Tattile cameras are added in the BVMS installation. This service uses an OpenSSL library, which has multiple vulnerabilities as published by OpenSSL. When successfully exploited, these vulnerabilities could lead to command injection or denial of service.
|
|
Publication
|
Git for Windows Multiple Security Vulnerabilities in Bosch DIVAR IP all-in-one Devices
|
|
DIVAR IP System Manager is a central user interface that provides an easy system setup, configuration and application software upgrades through an easily accessible web-based application.
|
2023
|
Advisory number |
Title |
Affected Products |
Summary |
|
Publication
|
Command injection vulnerability in Bosch IP Cameras |
|
A vulnerability was discovered in Bosch IP cameras of families CPP13 and CPP14, that allows an authenticated user with administrative rights to execute arbitrary commands in the operating system of the camera. |
|
Publication
|
Denial of Service vulnerability in Bosch BT software products
|
|
A security vulnerability discovered in Bosch internal tests allows an unauthenticated attacker to interrupt normal functions and cause a Denial of Service / DoS. Bosch rates this vulnerability with a CVSSv3.1 base scores of 7.5 (High) for products using the vulnerable function as a server and 5.9 (medium) for products using the vulnerable function as a client, where the actual rating depends on the individual vulnerability and the final rating on the customer’s environment. Customers are strongly advised to update to the fixed versions.
|
|
|
Remote Code Execution in RTS VLink Virtual Matrix
|
• RTS VLink Virtual Matrix Software
|
A security vulnerability has been uncovered in the admin interface of the RTS VLink Virtual Matrix Software. The vulnerability will allow a Remote Code Execution (RCE) attack. Versions v5 (< 5.7.6) and v6 (< 6.5.0) of the RTS VLink Virtual Matrix Software are affected by this vulnerability. Older versions are not affected. The vulnerability has been uncovered and disclosed responsibly by an external team of researchers. |
|
|
Multiple Vulnerabilities PRA-ES8P2S Ethernet-Switch
|
• Bosch PRA-ES8P2S < 1.01.10
|
Multiple vulnerabilities were found in the PRA-ES8P2S Ethernet-Switch. Customers are advised to upgrade to version 1.01.10 since it solves all vulnerabilities listed. Customers are advised to isolate the switch from the Internet if upgrading is not possible. The PRA-ES8P2S switch contains technology from the Advantech EKI-7710G series switches. |
|
|
Update in Cybersecurity Guidebook of BIS on Permission Settings for Network Share
|
• Bosch BIS
|
In a recent survey of BIS installations worldwide Bosch identified that for some installations the security settings may not meet our recommended security standards. For this reason, we have updated our "Cybersecurity Guidebook". Section 4.5 of the Cybersecurity Guidebook describes how to configure access permissions for a shared folder of the BIS installation. In an older version of the Cybersecurity Guidebook, one of the recommended access permissions is wrongly stated as "Network" group instead of "Network Service" group. This information is updated in the new version of the documentation, because executing the earlier instructions may unintentionally grant access permission to potentially unauthorized users. This is not a software bug, just an update of the documentation targeted at installers. This document is included in BIS installation folder since version BIS 5.0. Previous BIS version do not contain the document, but validating the security setting is generally advised. |
|
|
Information Disclosure Vulnerability in Bosch IP cameras
|
• Bosch Camera Firmware
|
An information disclosure vulnerability was discovered in Bosch IP camera devices allowing an unauthenticated attacker to retrieve information about the device itself (like capabilities) and network settings of the device, disclosing possibly internal network settings if the device is connected to the internet. This vulnerability was discovered by Souvik Kandar and Arko Dhar from Redinent Innovations, India |
|
|
Possible damage of secure element in Bosch IP cameras
|
• Bosch Camera Firmware
|
Due to an error in the software interface to the secure element chip on the cameras, the chip can be permanently damaged leading to an unusable camera when enabling the Stream security option (signing of the video stream) on Bosch CPP13 and CPP14 cameras. The default setting for this option is "off". |
|
|
.NET Remote Code Execution Vulnerability in BVMS, BIS and AMS
|
• Bosch AMS |
The Bosch Video Management System (BVMS), the Bosch Access Management System (AMS), and the Bosch Building Integration System (BIS) are using a vulnerable version of the Microsoft .NET package System.Text.Encodings.Web. The System.Text.Encodings.Web is a NuGet package from Microsoft, and Microsoft has published an advisory to provide information about a vulnerability in System.Text.Encodings.Web. A remote code execution vulnerability exists in System.Text.Encodings.Web due to how text encoding is performed.
|
|
|
Vulnerability in Wiegand card data interpretation
|
• Bosch AMS
|
Bosch Access Control products AMC2-4WCF and AMC2-2WCF have a firmware bug which may lead to misinterpretation of access card data that is sent from a Wiegand reader. This may in turn lead to granting physical access to an unauthorized person. This vulnerability affects only products with Wiegand interface, i.e., not devices with OSDP / RS485 interface. |
|
|
Unrestricted SSH port forwarding in BVMS
|
• Bosch BVMS |
The Bosch Video Management System is using SSH server that does not restrict a port forwarding requested by an authenticated SSH client. An authenticated SSH client can request a connection which is forwarded by the BVMS SSH server to a resource within the trusted internal network, which is normally protected from the WAN interface. The resource can be beyond the scope of the Bosch Video Management System.
|
|
|
Insecure authentication in B420 legacy communication module
|
• Bosch B420
|
An authentication vulnerability was found in the B420 Ethernet communication module from Bosch Security Systems. This is a legacy product which is currently obsolete and was announced to reach End on Life (EoL) on 2013. The B420 was last sold in July 2013 and was replaced by the B426. An EoL notice was provided to customers. The B420 does not allow for direct access to the panel as this module does not allow direct connection to the SDI/Option Bus that communicates directly with the panel. __ However, customers that are still using this device are advised to replace it for the B426 to ensure it is connected in a secure network. |
*CVSS - Common Vulnerability Scoring System

See below how you can do that:
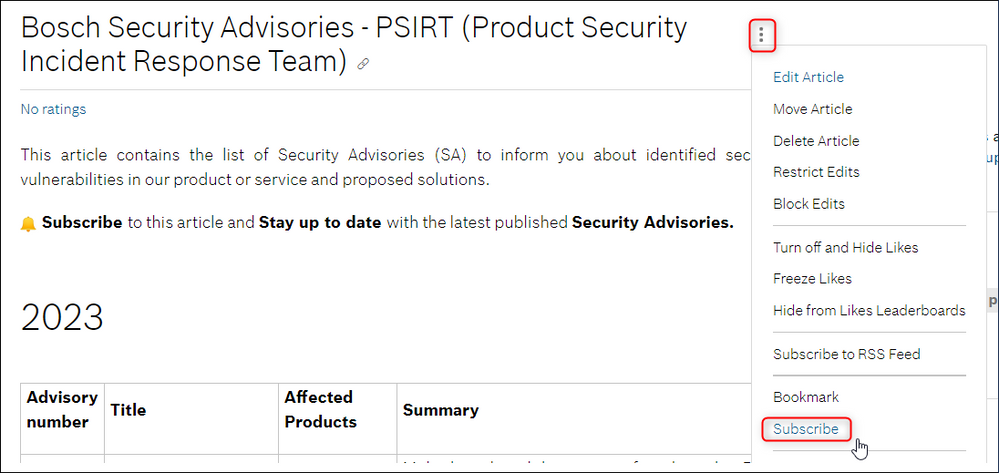
1. Access the Bosch PSIRT Security Advisories website
2. Scroll down to the RSS Feeds section on the page > right click on the Security Advisories Category you want to receive notifications for > copy the link address:
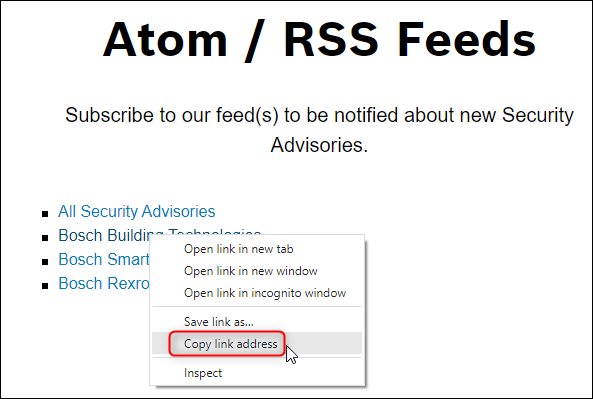
3. Go in Outlook and search for "RSS Subscriptions" option > right click on it > select "Add a New RSS Feed"
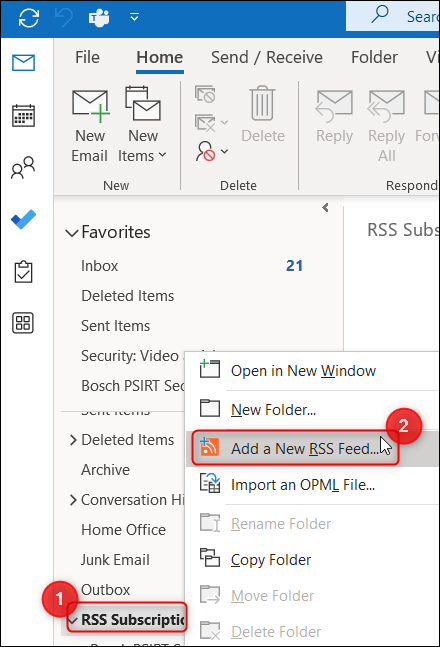
4. Paste the link you just copied before from the Bosch PSIRT Security Advisories website > click Add
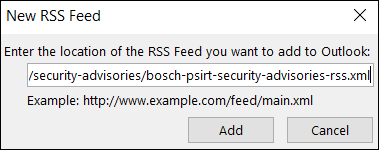
5. Click Yes
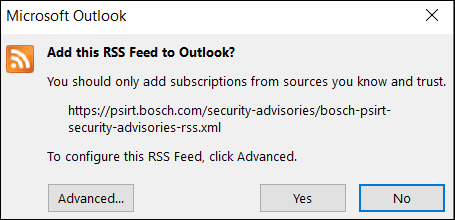
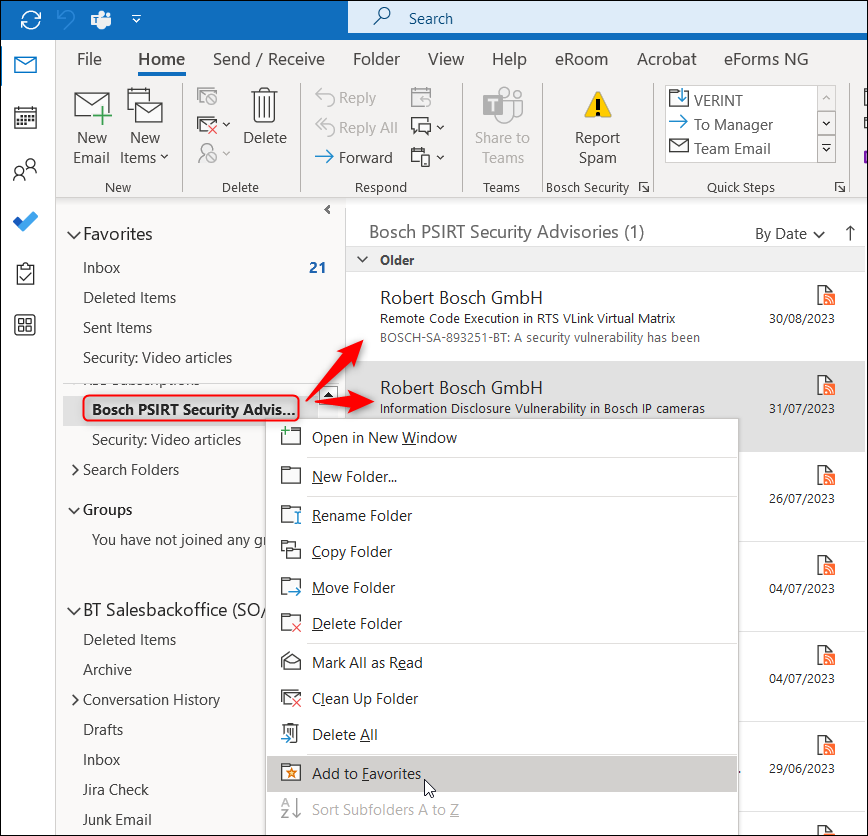
6. Now, you will be notified every time when a new Security Advisory is published.
Once the RSS Feed is added to your Outlook, you will see the latest Security Advisories. You also have the option to add this folder to Favorites.

Still looking for something?
- Top Results